Indigo DQM Data Asset Store is a database that contains all the Data Command Queries, Data Folders, Data Sources, Data Reports, Data Execution Plans and Execution Logs in a shared Data Asset Repository.
Its purpose is to consolidate Data Assets into a shared repository for the most efficient and effective data management and reporting.
Data Consolidation allows the collection and integration of data from multiple sources and types into a single destination. During this process, different Data Sources and types are put together, or consolidated, into the Indigo DQM Data Asset Store.
Indigo DQM allows multiple Data Assets Stores to be configured with Data Asset Stores Tool. Data Stores can be easily added, edited, deleted and activated.
The Indigo DQM Data Asset Store allows Data Queries, Data Sources, Data Reports and Execution Plans to be organized into Data Folders for the most effective management and availability of Data Assets.
Configuration of multiple Data Asset Stores
Multiple Data Asset Stores can be setup and activated / switched for different Data Projects using the Data Asset Stores Configuration Tool.
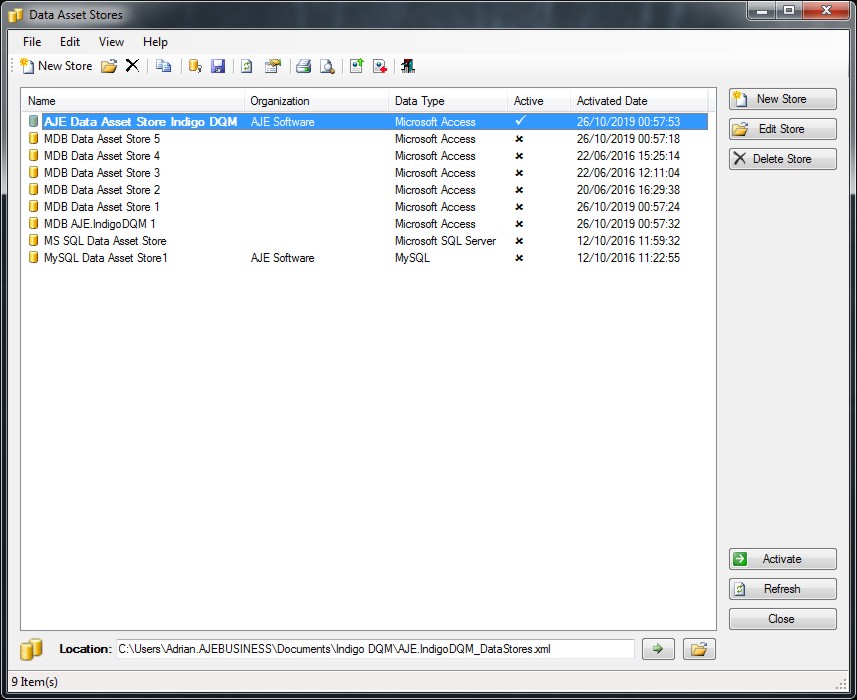
To activate the Data Asset Store click the 'Activate' button and the Data Store will become then active.
Indigo DQM Data Asset Store supports multiple Data Sources and types including Microsoft SQL Server, Microsoft Access and MySQL.
Data Stores can be migrated to any of these other types using the inbuilt features of the system or with the tools provided with your database.
Default Data Asset Store
Initially the system comes with a default Data Assets Store as an MDB Database which is installed in the User Documents Folder.

This can be moved to any location including a network share. The Data Store may also reside on another type of database such as Microsoft SQL Server or MySQL.
You can migrate the Data Asset Store to another database using the built-in migration features of the system or with the tools provided with your database.
Adding a Data Asset Store
Adding a new Data Asset Store using a Microsoft SQL Server Database. Enter the details for the new Data Asset Store including a description and reference.
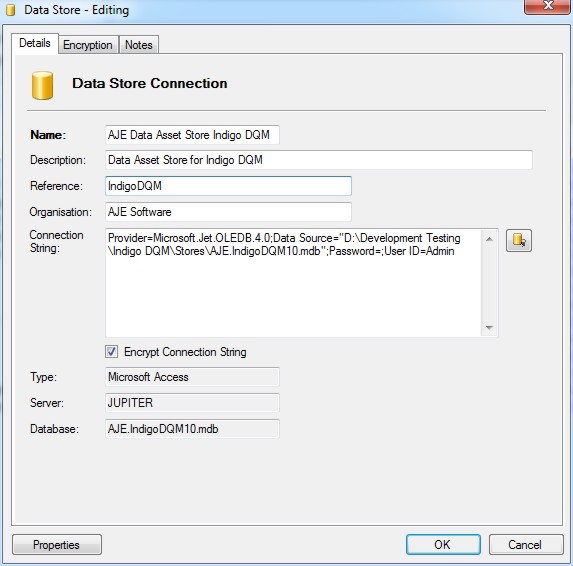
Specifying the connection parameters to the Data Store using the Connection Dialog.
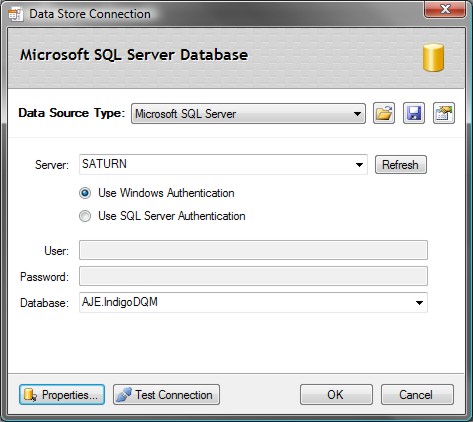
Connection Strings can be saved or opened into the Data Connection Dialog.
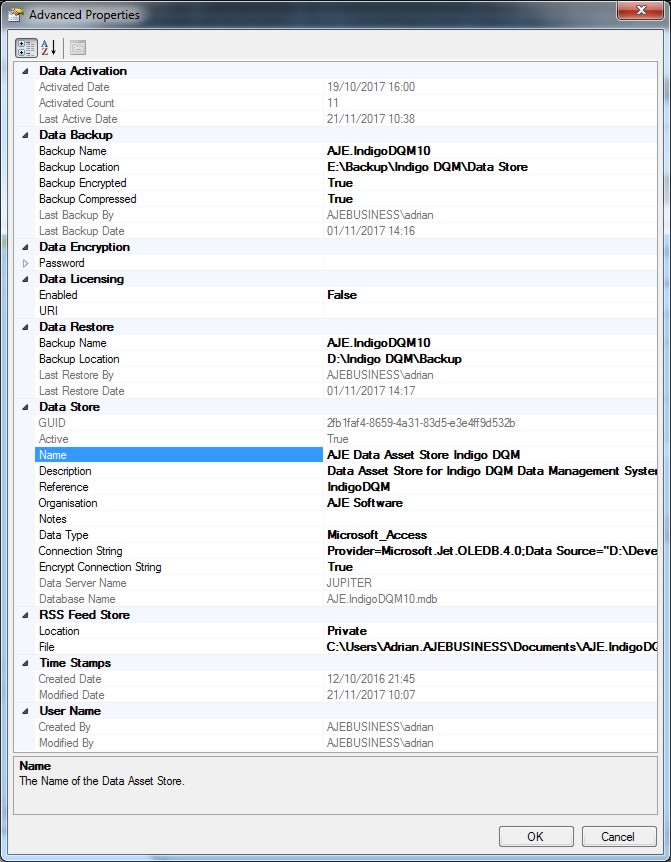
Data Store Properties
Advanced properties of the Data Asset Store allow the configuration of additional settings.
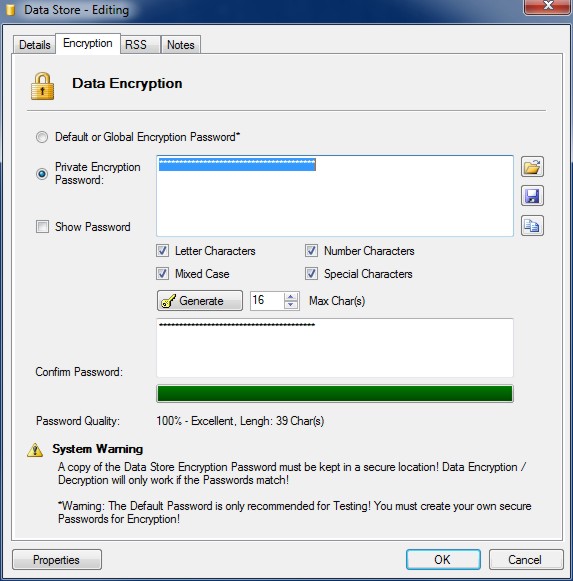
Data Encryption
Indigo DQM features AES 256 Advanced Encryption Standard allowing Data Assets to be stored and transmitted across the Internet / Cloud in the most secure way possible.
Data Result Outputs, Data Source Files, Raw Data and Backup Data can be encrypted and stored securely using the highest level of cryptography.
Encryption can be setup globally in 'Program Settings and Options' or applied to an individual Data Asset Store where a private encryption password will be used to encrypt data.

To use a private encryption password on the Data Asset Store select the radio button and enter a strong password.
Click the 'Generate' button to automatically create a strong encryption password. The strength of the password is shown by the bar.
Great care must be taken to keep copies of encryption passwords in a secure location. If you lose your password you will not be able to decrypt your data. You must also remember what password you used to encrypt data if you decide to change the password at a later stage. Encryption / decryption will only work if the encryption passwords are the same.
The Advanced Encryption Standard (AES) 256 is a symmetrical encryption algorithm that uses a 256-bit encryption key. It is accepted by the U.S. and Canadian governments as the most secure way to store sensitive data.
With AES-256 bit encryption you can be assured that you will be the only one who can access your critical information.
Data Store and System Status
Information on the current Data Asset Store, System Status and System Log can be viewed on the System Status dialog.

Status showing details about the current active Data Asset Store.
NOTE: The default encryption password should only be used for testing! You must generate your own secure encryption password!

